WeRedirect APT. The Large-Scale Scam Attack: Exposing the Elaborate Tactics of Online Scams Part III
- Debunk.org
- Dec 29, 2023
- 17 min read
Updated: Dec 4, 2024
In the third instalment of the investigation into the biggest scam and disinformation attack in Lithuania to date, our analysts uncover the intricate technique of “cloaking” used by the scammers. This method makes detection of the scam even more challenging, as it involves creating many different websites or webpages and, depending on specific criteria, redirecting different users to different content.
Introduction
Researchers from Debunk.org have uncovered a concerning trend in Lithuania and several other European countries. It has been found that online scammers are replicating prominent news portals and creating fraudulent Facebook accounts to deceive individuals into investing in fake platforms, ultimately defrauding innocent citizens of their hard-earned money.
Unidentified individuals are exploiting the brands of LRT, LNK, Delfi, InfoTV, the Estonian national broadcaster ERR, the Estonian newspaper Eesti Päevaleht, Widomości, a news program on a Polish public television station, one of the largest Polish internet portals Onet.pl, and many others.
Scammers are also using brands like Ignitis, the biggest energy company in Lithuania, Swedbank, Danske bank and Orlen Lietuva, creating fake copies of their accounts, and displaying fraudulent advertisements under their name. For a similar purpose they also use, e.g., a strategic gas infrastructure project - The Baltic Pipe Project.
These activities aim to induce Facebook users to participate in fake investment schemes.
Read more in Part I of the investigation:
To attract the attention of more people, advertisements offering quick financial success often use recognizable faces, such as performers, journalists, politicians, celebrities, and influencers.
Unfortunately, fraudsters even use deepfakes, and such manipulated videos have been appearing with increasing frequency. Politicians are often featured in these videos. For example, there were deepfake advertisements promoting fake investments with the Lithuanian President Gitanas Nausėda, as well as Polish President Andrzej Duda, former Polish President Aleksander Kwaśniewski, and Spanish presenter Lorena Castell.
Read more in Part II of the investigation:
Below, we present Part III of this investigation, where we expose The WeRedirect APT and the cloaking technology: intricate methods employed by criminals to conceal their activities, making detection even more challenging.
In cybersecurity, Advanced Persistent Threats (APTs) typically refer to highly sophisticated, sustained, targeted cyber threats. APTs are typically named based on various criteria such as characteristics, tactics, techniques, or attribution details. Names can vary and are often assigned by cybersecurity researchers, organisations, or the security community. These names aim to provide a clear reference to a specific threat actor or campaign.
Throughout our investigation, we have uncovered the cunning tactics used by scammers. As previously mentioned, they skillfully impersonate well-known media portals and brands, exploiting real-life tragedies and celebrities to attract audiences and lure them into fake investment platforms. Furthermore, they employ various techniques to conceal their content on social media platforms, making its removal difficult and enabling them to evade detection in their fraudulent operations.
In this section, we will also highlight the shortcomings of Meta's anti-fraud measures. Our research suggests that Meta's current approach is inadequate, enabling criminals to take advantage of its platforms and profit from fraudulent activities. We recommend that Meta revise its strategy to effectively prevent these fraudulent activities. Failure to do so not only endangers users but also inadvertently supports criminal activities that continue to generate profits from scams.
Cloaking technology used by scammers
The WeRedirect APT threat actor investigation revealed that criminals utilise "cloaking technology" in the realm of online fraud and deceptive practices. This technology involves scammers designing a website or webpage to present distinct content to different users depending on specific criteria. The server is responsible for determining which content to deliver, employing a decision-making mechanism that analyses various parameters to determine what a particular viewer should see.

Researchers have found evidence that scam websites are configured to dynamically generate content, depending on the parameters provided:
Multiple redirects: Scammers have devised a system in which a URL redirects users to various landing pages depending on specific conditions. For instance, a scammer may possess a URL that directs a search engine bot to a seemingly legitimate page (in order to enhance search engine rankings or evade detection), but redirects an ordinary user to a harmful or deceitful website. A server equipped with a decision-making mechanism determines the content that will be presented to the user.
User detection: Scammer's system detects various attributes of the visitor, such as the IP address, user-agent (which identifies the browser and operating system), type of device (e.g., smartphone, tablet), and other headers sent by the browser. It also considers information stored in cookies that reflect the user's website interactions, session parameters (activity, time spent), and other conditions for example, using VPNs and blocking such users. This information is utilised to determine whether the visitor is a regular user, a search engine bot, or falls into another category, e.g., a researcher.
For example, when Debunk.org researchers repeatedly visited scam sites, after a prolonged period of time, they found themselves almost exclusively on poor-quality facade news sites and articles containing advertising for fake investment platforms were not shown to them.
Content variation: Depending on the detection, different content is served. For a search engine bot, the content might be optimised for SEO to ensure good ranking and visibility while appearing legitimate. However, for a regular user, especially one identified as a potential target, the content might be a phishing page, a scam offer, or other deceptive material.
Purpose: The main objective of this technique in a scamming context is to avoid being detected by authorities, content moderators, and knowledgeable internet users who may report or flag the scam. By displaying genuine content to search engines and specific users, scammers can sustain their online presence and continue to exploit unsuspecting individuals.
Cloaking technology in action: redirects
By analysing advertisements for scam investments, analysts at Debunk.org observed many cases in which criminals used the redirection technique. Depending on the circumstances, the user would observe different content. They might see a copy of the real portal, e-shop, or organisation, allowing the user to navigate through its various tabs, but set up on a scam domain. As a result, the URL would not match the true one. Alternatively, they could be redirected to an imitation of a gossip page, but a quick assessment shows that the page is of very low quality and is basically just a facade. Finally, they might simply see an error message or a white screen.
Redirecting investigators and content moderators to harmless websites to mask real intents
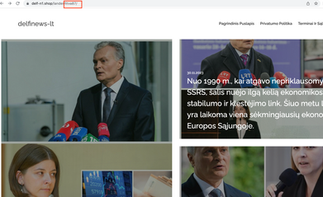
Below is an example of a redirect to a harmless website, such as a “cloned page” of an organisation, company, or e-store. Initially, the fraudsters purchased Meta advertising using a fake account named 'INFO Dienos', which was intended to appear as a news source. Within the advertisement, they included a link to a fraudulent article promoting investment scams. To avoid easy detection within their infrastructure, they employed geolocation/IP based redirection. Consequently, when a Lithuanian user clicks on the link, they are directed to the fake Delfi website and the fraudulent article, while non-Lithuanian visitors are redirected to another website. It is important to note that the URL remains the same in both cases. This serves as evidence that the website is merely an imitation, which can be verified by locating the genuine website and URL address (in this instance, the true address is elevenmiles.com).

Analysts observed this feature by using a VPN. By altering the IP address and country in the software, we were able to witness the deception of the fraudsters. Below is a recording of this observation.
Below is the documentation from several similar cases of redirection. In these instances, the scammers utilised, e.g., online shops, including an e-shop specialising in fishing accessories and another one dealing with cameras and electronics.


Researchers also analysed the chain of requests that occur while loading the page, which is visible in the network section of the developer tool built into most browsers. They noted that, in some cases, scammers link to the real domain to some extent. Usage of this technique can be observed on examples of websites pretending to be Lithuanian Klaipeda Rowing Centre, where researchers were redirected alternatively with the scam article.

The chain of requests that occur while loading the page is visible in the network section of the developer tool built into most browsers. Below, we present a screenshot from the network section of the developer tool while loading the website afnatree[.]com or website with a scam article in Polish - greenlightsjo[.]com
![The network section of the developer tool of the afnatree[.]com](https://static.wixstatic.com/media/e0954e_d4eef82993f9449bbfb720bd1079ed59~mv2.png/v1/fill/w_49,h_35,al_c,q_85,usm_0.66_1.00_0.01,blur_2,enc_avif,quality_auto/e0954e_d4eef82993f9449bbfb720bd1079ed59~mv2.png)
![The network section of the developer tool of the greenlightsjo[.]com](https://static.wixstatic.com/media/e0954e_2ebbb8ab261642fa99f0043f7dc2b040~mv2.png/v1/fill/w_49,h_26,al_c,q_85,usm_0.66_1.00_0.01,blur_2,enc_avif,quality_auto/e0954e_2ebbb8ab261642fa99f0043f7dc2b040~mv2.png)
A user accesses the initial website (in this case, afnatree[.]com), and the browser loads the corresponding resources.
In the background, the website initiates requests to a different domain (klaipedosirklavimas.lt) to fetch additional resources.
The purpose of this technique is to obscure the true origin and purpose of the requests. By routing traffic through seemingly legitimate domains (such as klaipedosirklavimas.lt), scammers aim to avoid detection by security tools that might flag or block known malicious domains.
Domain shadowing involves creating subdomains dynamically or using compromised accounts on legitimate services to set up these shadow domains. This technique allows scammers to rapidly switch between different domains, making it harder for security teams to track and block malicious activities.
Redirection to poor quality, facade news websites
In case of geolocation mismatch the scammers redirected selected users to a second group of portals, which were websites of extremely low quality. These portals were created in large numbers, following specific patterns. They appeared similar to 'gossip sites', but contained only a few articles that were short and very general. Additionally, stock photos were included on these sites. Although the title and picture on these portals were usually similar to the advertisement, the actual article itself was very brief and of poor quality. Furthermore, it did not provide any references to the scam.

Redirection: page becomes unavailable
The latest version of "redirect" simply renders the URL inaccessible when the user is not in the desired location. In such cases, they will encounter an error message or a blank screen.

Diverse Content Variations
In our investigation, we came across scam articles with varying content and were also redirected to various poor-quality websites. Manipulating the URLs of one of them allowed researchers to discover that they actually saw completely different versions of facade pages, including differences in layout and content, depending on the URL path (see below) [1].
Examples of how changing the URL path results in different content being displayed on the same domain
Significantly, we discovered that the websites were not only linked within Lithuania but also internationally. During our analysis, we encountered low-quality pages in various languages, including Lithuanian, Swedish, Latvian, and English, and identified the sources responsible for such content.
Interestingly, we found that in certain domain groups, these paths could be used interchangeably. For instance, if the path responsible for the Swedish version of a content (e.g., /lander/se1-vlad) is connected with the domain initially found in Lithuanian and with Lithuanian 'articles' (e.g., delf-n1[.]shop), the Swedish version is launched (delf-n1[.]shop/lander/se1-vlad/). The fraudsters create these pages using a template, only altering the local context of the content. As mentioned, the facade pages are of very poor quality, consisting of a few short texts and a few images. The translation is clearly automated (see examples below).


What is more, the nomenclature of URL paths suggests a potentially extensive database structure. For instance, the path 'lander/se1-vlad/' is associated with the Swedish version. Here, 'se' serves as the country code abbreviation, and '1-vlad' denotes the version of the content. Similarly, in the Lithuanian version represented by the path 'lander/lt9-vlad/', 'lt' is the country code abbreviation, and '9-vlad' signifies the content version. Slightly different is the path for the English version, coded via ‘lander/dk1’ or the version in Latvian, ‘lander/kri--j--nis-kari------lv--white2’. Different paths can point to different folders where resources or content tailored to specific countries or language versions are stored. The server has access to a bunch of different variants and chooses one depending on the parameters.
The researchers also discovered that criminals use templates for scam advertising pages. Although the stories change, the names of the alleged investment platforms, people, and media outlets, the goal remains the same - to grab attention and find a victim. Scammers, among other things, use an analogous text structure, the same images and only modify their descriptions depending on the context. This can be seen very well in the example below the images - the "journalist" is called differently in different countries (although in the case of Poland and the Czech Republic he even has the same first and last name), and the images differ only in the content visible on the man's computer. Using reverse image search, the researchers found around 100 articles using an identical image of a 'journalist': https://nimb.ws/Cm5Lqf.


The scam articles also use, for example, templates of alleged bank statements. Below is an example of how some of the data has been changed depending on the country, sometimes the logo of the real bank has been added, while other data, such as account number, account, country classification code, has at times been left the same.

This discovery again proves the connections between the various cases. Observations reveal that the scammers, utilising the same server or hosting infrastructure, use article templates in different countries - very similar text structure, content, same images, etc. and operate not within a single country but across multiple countries. Their aim is to target the largest possible audience and deliberately confuse researchers and platforms by inundating them with thousands of domains and websites.
At the same time, it should be emphasised that there is also a possibility that scammers operate as a large group with local representatives in different countries or try to pretend that they are ‘locals’. This would be indicated not only by contextually demanding knowledge (political, social, various local tragedies, etc.) but also by content tailored to local audiences. Researchers discovered the use of slang Lithuanian language to describe elements on the website.
In a detailed analysis of one of the websites, it has been revealed that individuals who speak Lithuanian are orchestrating a disinformation campaign targeted, among others, at Ignitis. This conclusion was drawn after a thorough examination of the website’s HTML source code. The code revealed that images of several prominent figures, including DELFI journalist Erika Venckutė, Ignitis Group Director Darius Maikštėnas, and attorney Gintaras Černiauksas, were labelled with derogatory terms. These terms included “Gaidys”, a Lithuanian term meaning “a cock”, “Zertva”, a derogatory Russian slang term translating to “bitch”, and “Lopas”, which translates to “an idiot” in English.

Similar observations have been noticed in the case of scam sites in Poland, where some of the elements displayed on the page have been described in Polish (see example below). [2]

What is more interesting is that sometimes languages 'cross over' on the websites of different countries, and so Lithuanian nomenclature was also found in the photo description of a scam website in Polish, impersonating the Polish Internet portal Onet.pl. One of the images was described as “zudikas” - in Lithuanian “žudikas” , which means “a killer” (see below).

(URL) Path to a scam
Upon further analysis of the source code, it was discovered that the URL path responsible for displaying the fraudulent article provided additional evidence of the connections between different domain groups, including low-quality and fake ones, and scam articles.
First, the analysts used developer tools in the web browser, such as the 'Inspect' option and the 'Network' tab, to analyse the traffic and interactions between the browser and the server. These tools allow for tracking network requests, analysing server responses, and exploring the various paths, parameters, and data sent between the browser and the server. The analysts discovered the aforementioned paths on poor quality sites, for example: nelopan[.]store/lander/mariyounas_lt_white2

Then researchers found an active scam article and checked the URL path there, e.g., w.sepcezear[.]com/lander/mariyounas--lt--fortune_1692612516/

In the end, we combined a low-quality domain with the URL path extracted from the scam article (nelopan[.]store/lander/mariyounas--lt--fortune_1692612516/). Surprisingly, the link was active and redirected to a scam article on a low-quality website, even though it was not initially visible there. This action revealed that such a manoeuvre leads to the display of the scam article on a 'junk' domain.

The procedure also worked for other poor-quality, bogus pages. Adding the mentioned path responsible for the scam article caused it to be displayed. This way, we have uncovered a complex and sophisticated infrastructure used by scammers.

However, the mechanism described above did not work for all domains, which led us to hypothesise that cybercriminals, either acting together or separately, create groups of directly linked domains served by the same server. They store different content variants, which are displayed to recipients based on the server's decision using certain aforementioned criteria.
WHO.IS who? Nobody knows
In addition to concealing their activities, scammers also attempt to hide their identity. One common method used by criminals is to conceal all data related to the domain used for their criminal activities. Analysts have used a WHO.IS tool to investigate suspicious domains. As expected, the vast majority of data was listed as 'non-public'. However, some metadata, such as the date of registration, could not be removed. This helped to establish that certain domains were most likely coordinated by the same individuals, as they were created within a very similar time frame (sometimes within a few seconds). Many of the suspicious domains exploited the names of well-established Lithuanian media providers, particularly Delfi, while others targeted company names, such as the energy provider in the region, Ignitis. The chart below displays the number of scam domains registered per month. The highest peak occurred in September 2023 when 38 malicious domains from the analysed sample were created.

The scammers utilise various cloud infrastructures, primarily Cloudflare, Digital Ocean, and hosting companies, to register fraudulent domains. These domains are registered through offshore companies such as Namecheap INC, Tucows, or URL Solutions, which are located in countries like Panama or Saint Kitts and Nevis. The scammers employ Cloudflare to hinder a thorough understanding of the domain structure and potential operational path. Cloudflare, a widely-used cybersecurity and performance enhancement service, is used by the scammers to prevent any efforts to scrutinise the complexities of their domain infrastructure.
The other address that appeared frequently in the database was the capital of Iceland, Reykjavik. However, a few scam domains revealed yet another location - the Kaunas region. It's important to note that these addresses offer minimal insights, mainly indicating that the scammers utilised an intermediary to register the domains, maintaining a veil over their true identities.

We have also investigated the IP addresses associated with the registration of these domains. However, it is important to note that having a common IP address does not necessarily prove coordination, as multiple domains can be hosted on the same IP. Additionally, some domains were hosted on servers commonly used to protect client privacy. One notable example is Njalla, a service that offers anonymous domain registration. Njalla was founded by Peter Sunde, the co-founder and former spokesperson of Pirate Bay, a popular torrent website. Njalla is operated by a company called 1337 LLC, based in Saint Kitts and Nevis. They provide domain hosting services on servers with the following addresses: (1) you.njalla.no, (2) can.njalla.in, (3) get.njalla.fo.
Interestingly, when the first and last parts of these server addresses are combined, it translates to "You can get no info" (by first reading the first part of the name of each of the three servers in turn and then the last parts - see below.)

However, measuring the timestamps between the time of registration of domains that shared other similarities (e.g., similar domain names impersonating Lithuanian media, the fact that they were used to spread the same scam articles, etc.) indicated a pattern that allowed tracking down domains used for the same scam operation.
These findings collectively underscore the extensive measures taken by the criminals to conceal their activities, creating formidable barriers that impede efforts to unveil their identities and establish culpability in the various scam campaigns. The complex web of registration tactics, IP address concealment, and the use of protective services like Cloudflare illustrates the sophisticated nature of their operations, making it challenging to attribute the scams and hold the perpetrators accountable.
META's administrators take no action, even after scam infrastructure reported
Restricting the activities of cybercriminals is a challenging task that necessitates constant monitoring of suspicious actions and the development of countermeasures against scam operations. [3] Debunk.org reached out to the Lithuanian Radio and Television Commission (Lietuvos Radijo ir Televizijos Komisija) regarding an online scam and requested the geo-blocking of domains used by APT WeRedirect for Lithuanians. Additionally, Debunk.org reported research findings to the Lithuanian National Crisis Management Center (NKVC), under the Lithuanian Government. NKCV officially requested META representatives to start an internal investigation and remove these threats. Unfortunately, META representatives did not respond, further allowing criminals to continue their activities on the META’s platforms. It should be noted that META also profits from scam advertisements. This means that META not only benefits from not blocking fraudsters but also generates revenue from advertising. Despite the company's claim to remove fake pages, scam ads, and links, many of them are still operational, and new ones flood social networks every day. The lack of cooperation with META is the biggest problem. [4]
Debunk.org also presented research to the Communications Regulation Council and the Seimas Committee on Culture. They declared their intention to prepare an appeal to the European Commission to review potential violations of the Digital Service Act (DSA). META should develop an anti-crime policy and offer a safe way to use social media platforms.. It should be emphasised that criminals are reaching a large audience and harm new victims. [5]
Conclusions
The conducted investigation is just one example of the scams that lurk online every day. Despite the increasing education and awareness on the subject, there are still many people who fall for the temptation of making "easy money" and getting rich without any effort. People tend to have a glimmer of hope that the unbelievable story they read online is true. This is exemplified by a user who asked the following question:
“Hello, I would like to ask if you have heard of the investment platform oil profit? Now there is information on a fake page of Delfi that Mykolas, the boy who disappeared and the police searched in the river, was allegedly murdered for the money he earned by oil profit. I signed up on the platform and immediately the consultant called me, and he was very chatty, very nice and sweet, and asked me questions about everything. He saw that I wasn't very talkative, so he started asking me about hobbies, about future purchases. Also where I live, where I work, what I do. What my income is, what my bank is. Whether I have a husband. When the conversation got to the point of sending me the details for the first deposit, I dropped the receiver, and then she wrote a couple of messages on viber, and I blocked her. Somehow I don't believe in such easy earnings. Have you heard of it? Maybe you have come across a similar situation?”

Users commenting on the post admitted that they had also signed up for the campaign and were now receiving persistent calls from unknown phone numbers. One person had even blocked over a dozen numbers that were harassing her about it. Another one mentioned that the caller had an Indian accent, which, along with the presence of photos of people from India among accounts sharing malicious links, could be a clue connecting the issue to that country.
The amount of money Estonian citizens invested in fake platforms over a three-month period is an indication of how many people fall prey to scammers and the impact of Meta advertising. According to an investigation by Eesti Ekspress, during the wave that started in mid-June, Estonians were exposed to at least 583 different fake ads, which have been viewed almost 2.5 million times so far. Journalists describe individual victims who invested thousands of euros in the scam, e.g. in connection with the ad with Elon Musk and Tesla - six victims lost in the scam between 46,000 and 2,000 euros. Ads with a former president of Estonia Kersti Kaljulaid prompted at least one person to invest and consequently lose as much as 9,069 euro. A number of people have lost money in larger and smaller amounts as a result of other advertisements and the spread of information about fake investment platforms on various social platforms.
In light of the widespread online scams, as detailed in this report, it is crucial to emphasise the importance of awareness and immediate reporting. Scammers, skilled at exploiting well-known brands and individuals, remain a significant threat. Meta's current measures are insufficient, and therefore, their casual approach needs to be reassessed. As users, it is essential to stay vigilant, report scams promptly on social media and fake websites, and foster a collective commitment to debunk such schemes. Importantly, during the course of our investigation, we came across a number of user warnings about the scam.
One of the commentators on the aforementioned posts provided valuable advice: one should report every such case, both on social media and on a fake domain. Another commenter added, "Don't get emotional. Ask yourself a simple question: if there are such astronomical earnings, then who would call people and offer them? They would invest their own 10 euros and become a millionaire. Who would work like that? This is not cryptocurrency or oil. You're just sending money to scammers."
The battle against online scams necessitates continuous awareness, which is the primary focus of the investigation and reports conducted by Debunk.org.
Stay safe, stay informed
In the face of rising online scams, your vigilance is a powerful tool against fraud.
Stay alert and be proactive – report any suspicious activities promptly. Your contribution is crucial in safeguarding not only yourself but also the wider online community.
Educate yourself to stay one step ahead. Share these resources with friends and family to create a collective shield against scams.
Remember, knowledge is the best defence in the digital age.
References
[1] See: https://nimb.ws/Q9SC6r
[2] In the example below, however, the description does not make sense, as the picture presenting celebrities known in Poland has been described as 'pociąg należący do pkp intercity', which means 'train belonging to PKP Intercity'.
[3] See: the BBC investigation on the Milton case: The Billion Dollar Scam - BBC World Service, BBC World Service, <https://www.youtube.com/watch?v=w6JXZ3GzSCQ&ab_channel=BBCWorldService>
[4] The problem of the Meta's inaction in countering scam adverts was also noted by researchers in Estonia, see: O. Kund, M. Vunš, Virtuaalne psühhoterror: Eesti kuulsuste nimesid kasutanud petised lollitavad ära nii ohvrid kui ka politsei, 7.11.2023, Eesti Ekspress, <https://ekspress.delfi.ee/artikkel/120245667/virtuaalne-psuhhoterror-eesti-kuulsuste-nimesid-kasutanud-petised-lollitavad-ara-nii-ohvrid-kui-ka-politsei>
[5] See: J. Skėrytė, Lithuania to turn to EC as Meta ignores calls to deal with scammers on social media, 6.12.2023, LRT, <https://www.lrt.lt/en/news-in-english/19/2143013/lithuania-to-turn-to-ec-as-meta-ignores-calls-to-deal-with-scammers-on-social-media>